OpenVPN系列 - 对接OpenLDAP作统一认证

环境
- 操作系统: Linux
LDAP数据构造
创建两个测试账号
- zhang3.ldif
dn: uid=zhang3,ou=users,dc=vqiu,dc=local
cn: 张三
gidnumber: 2000
homedirectory: /home/zhang3
loginshell: /bin/bash
objectclass: inetOrgPerson
objectclass: posixAccount
objectclass: shadowAccount
sn: Linux
uid: zhang3
uidnumber: 2000
userpassword: {SSHA}E626//fgm2nTWqIvn/TaltqIZL5SCy54li4.ldif
dn: uid=li4,ou=users,dc=vqiu,dc=local
cn: 李四
gidnumber: 2001
homedirectory: /home/zhang3
loginshell: /bin/bash
objectclass: inetOrgPerson
objectclass: posixAccount
objectclass: shadowAccount
sn: Linux
uid: li4
uidnumber: 2001
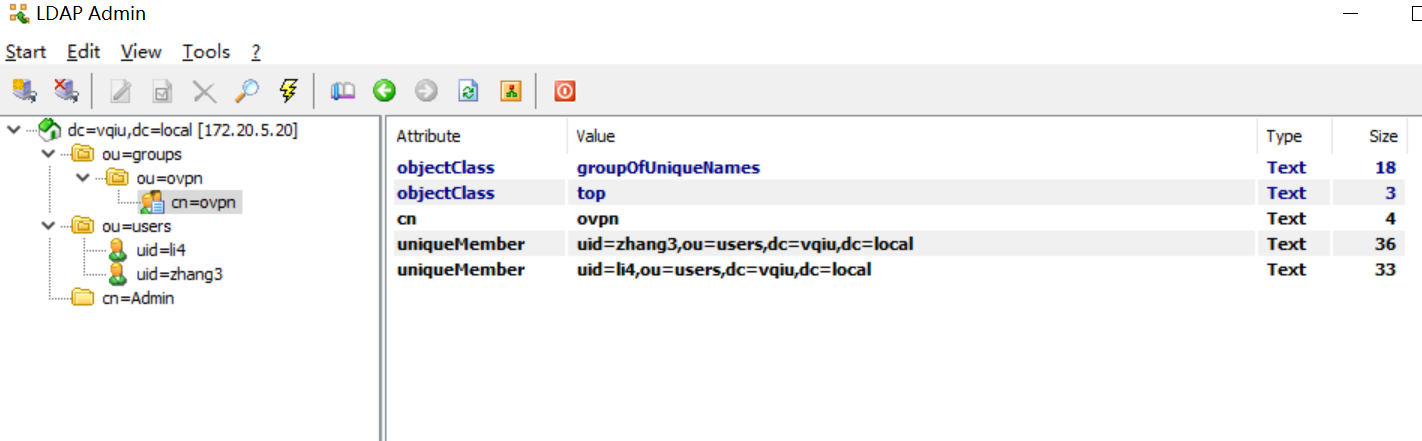
userpassword: {SSHA}JRCxn0ir/7vZGRWqp8Zrni+fanxgrVFe创建ovpn组,并关联上述用户
dn: cn=ovpn,ou=ovpn,ou=groups,dc=vqiu,dc=local
cn: ovpn
objectclass: groupOfUniqueNames
objectclass: top
uniquemember: uid=zhang3,ou=users,dc=vqiu,dc=local
uniquemember: uid=li4,ou=users,dc=vqiu,dc=local结构截图
服务配置
- /etc/openvpn/server.conf 新增内容如下:
plugin /usr/lib/openvpn/openvpn-auth-ldap.so /etc/openvpn/auth/ldap.conf
verify-client-cert none- /etc/openvpn/auth/ldap.conf
<LDAP>
URL ldap://xx.xx.xx.xx:389
BindDN CN=admin,DC=vqiu,DC=local
Password 密码
Timeout 15
TLSEnable no
#TLSCACertDir /etc/openldap/certs/
#TLSCACertFile /etc/openvpn/ca.pem
#TLSCertFile /etc/openldap/certs/server.crt
#TLSKeyFile /etc/openldap/certs/server.key
FollowReferrals yes
</LDAP>
<Authorization>
BaseDN "ou=users,dc=vqiu,dc=local"
SearchFilter "uid=%u"
RequireGroup true
<Group>
BaseDN "ou=ovpn,ou=groups,dc=vqiu,dc=local"
SearchFilter "(cn=ovpn)"
MemberAttribute uniqueMember
</Group>
</Authorization>客户端测试
zhang3.ovpn内容
client
dev tun
proto udp
remote IP 1194
resolv-retry infinite
nobind
persist-key
persist-tun
key-direction 1
remote-cert-tls server
ignore-unknown-option block-outside-dns
auth SHA512
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
verb 3
reneg-sec 0
auth-user-pass # 重点
<ca>
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
</ca>
<tls-auth>
#
# 2048 bit OpenVPN static key
#
...
</tls-auth>客户端文件(.ovpn) 中追加以下内容
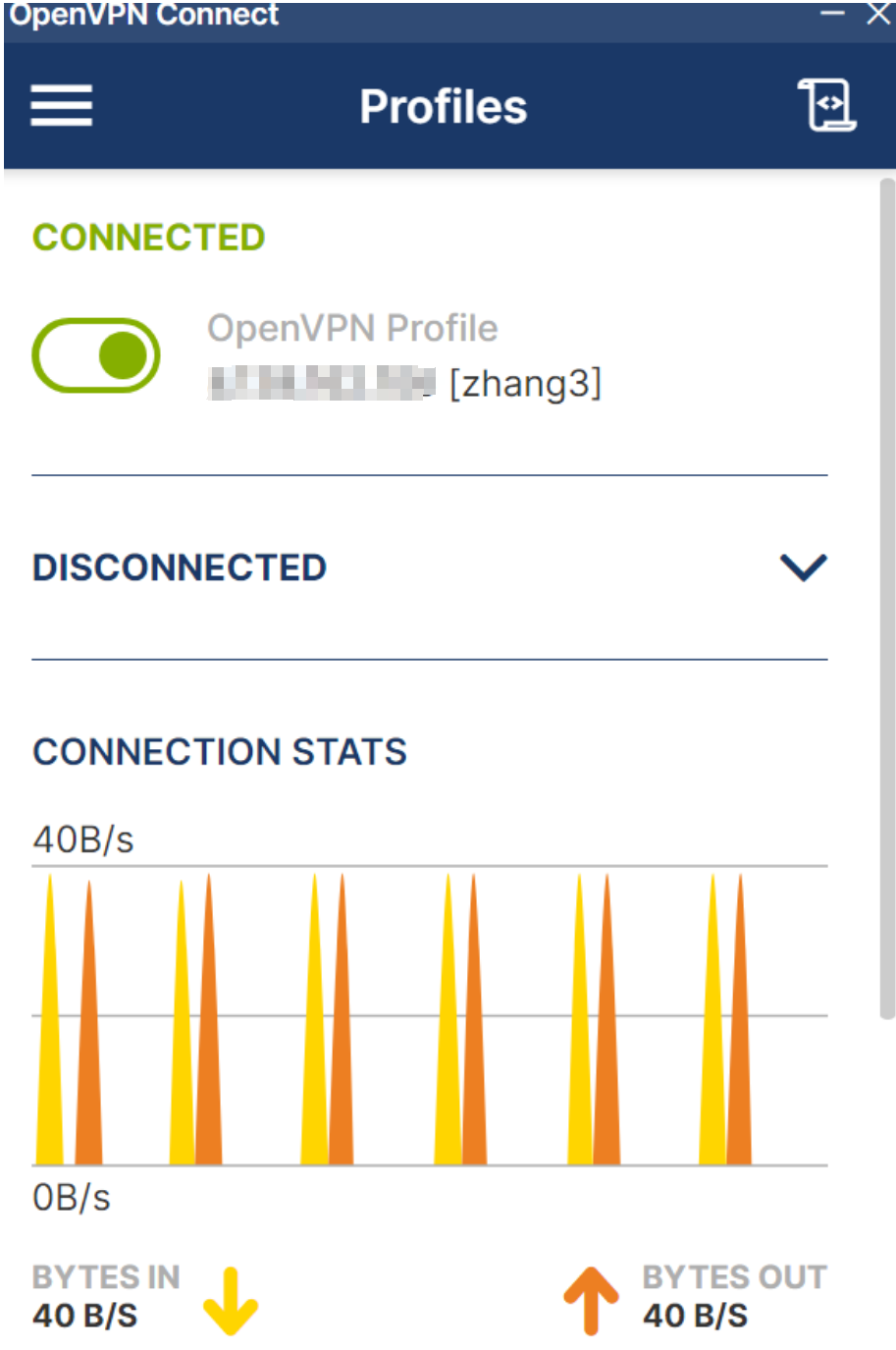
auth-user-pass如果配置正常的话,可以实现以下需求:
- 登陆直接使用LDAP中的用户名与密码
- 隶属于ovpn中的组都能登陆,如果将用户剔除组用户将无法正常登陆